SAML Single Sign-On (SSO) with Okta
Enterprise feature
Single Sign-On is available on our Enterprise plan. If you’re interested in learning more about an Enterprise plan, please contact us.
To set up Single Sign-On with Okta, you will need administrator access to your Okta organization.
1. Prepare Ybug for SSO configuration
1.1 Before you can set up the Okta application, you must open the Single Sign-On settings page in Ybug. Go to your Team account settings page, click the Single Sign-On tab and check the Enable Single Sign-On checkbox. Leave this window open, you will need this information to complete configuration of the Ybug app in Okta.

2. Set up Okta application
2.1 In your Okta Admin Dashboard click on Add applications.

2.2 On the following page, click the Create New App button.
2.3 Select Web as the platform and SAML 2.0 as a Sign on method.

2.4 Enter App name: Ybug, optionally upload a logo and click Next.

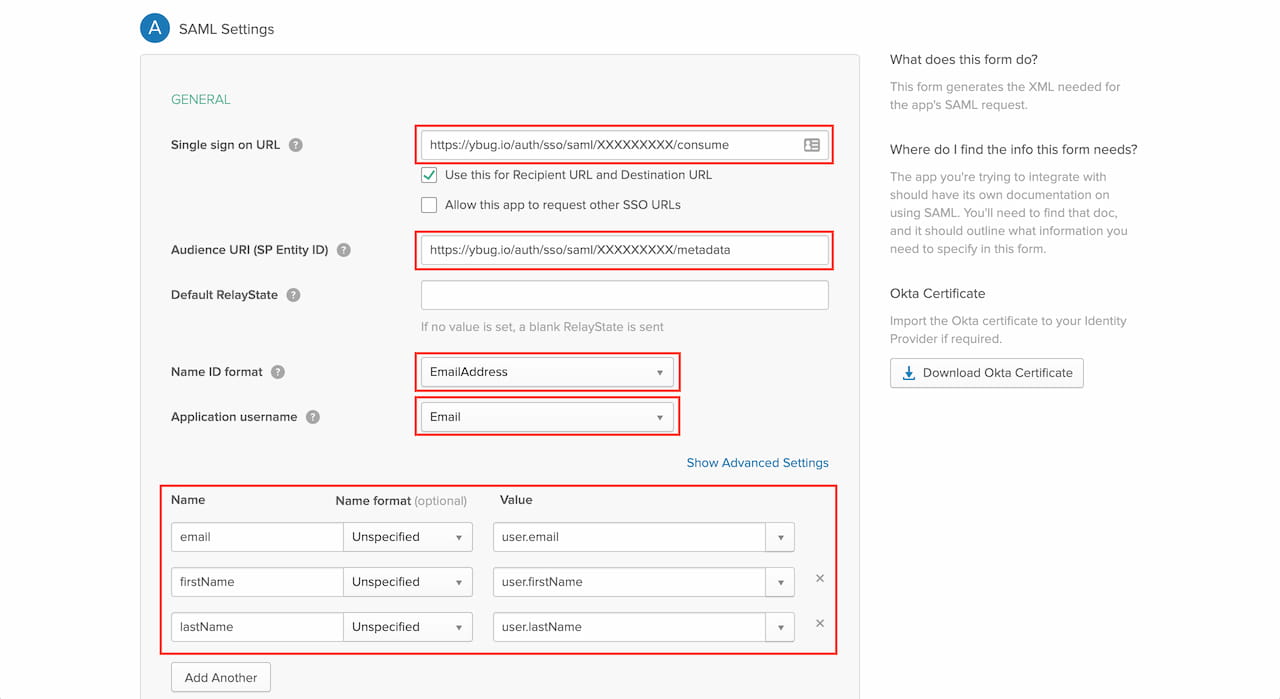
2.5 Configure the SAML integration. Enter the Ybug service provider details from the Ybug Single Sign-On page (from the Step 1). Also make sure to add the email, firstName and lastName attributes as depicted on the following picture.
| Field (in Okta) | Value (from Ybug) |
|---|---|
| Single sign on URL | Assertion Consumer Service URL |
| Audience URI (SP Entity ID) | Entity ID |
| Name ID format | Select EmailAddress |
| Application username | Select Email |
2.6 Click Next, Select I'm an Okta customer adding an internal app and click Finish.
3. Set up Ybug
3.1 On the Okta application settings page, go to Sign On section, click the View Setup Instructions button.
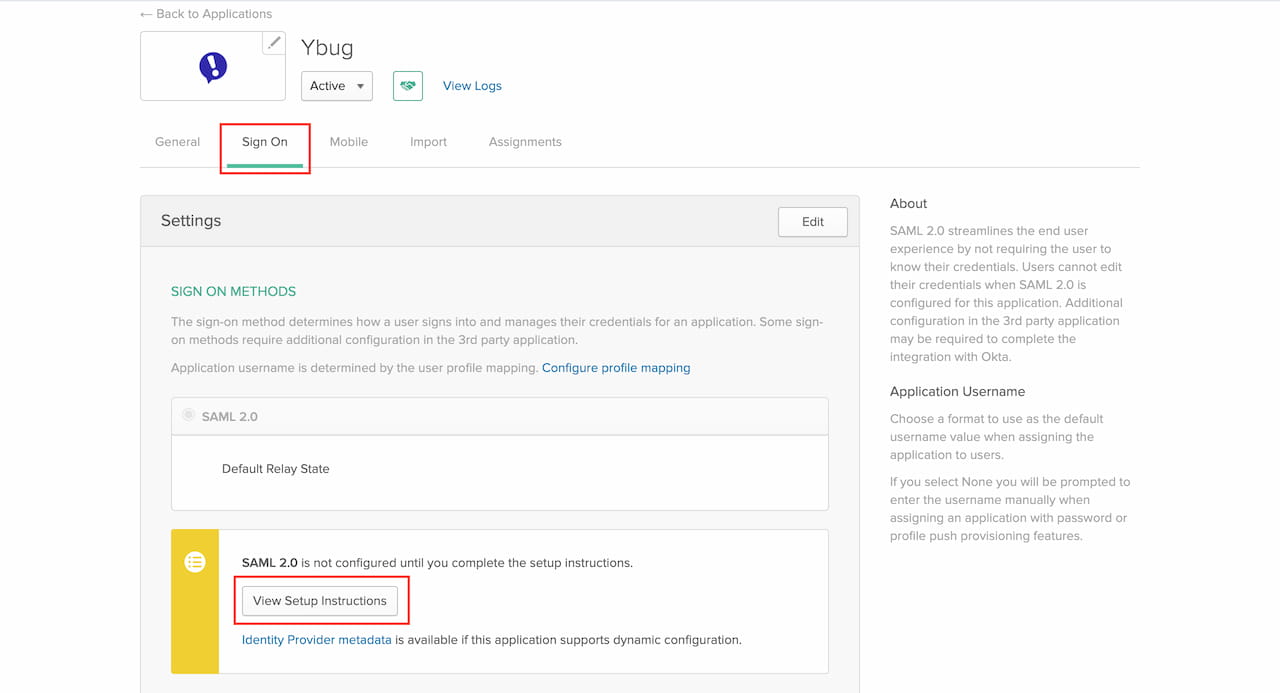
3.2 Copy and paste the values of Identity Provider Issuer, Identity Provider Single Sign On URL and X.509 Certificate into Ybug.
| Field (in Ybug) | Value (from Okta) |
|---|---|
| Entity ID | Identity Provider Issuer |
| SSO URL | Identity Provider Single Sign On URL |
| Certificate | Contents of X.509 Certificate |

3.3 Then in Ybug click the Save SSO Settings button to enable the Single Sign-On.
4. Assign users
Assign users to your new Ybug SAML application in Okta.
Final steps
After successfully setting the SSO, your users should be able to sign in or sign up using your Identity Provider.
- Team members (not owners) with an existing Ybug account with the same email address as their SSO account will be switched to SSO authentication after they first log in with SSO.
- For users who do not have Ybug account yet, a new Ybug account will be provisioned once they log in for the first time (from their Identity Provider).
Do you have any questions?
Contact us in case you have any questions or feedback.
We will be happy to help.