SAML Single Sign-On (SSO) with Azure AD
Enterprise feature
Single Sign-On is available on our Enterprise plan. If you’re interested in learning more about an Enterprise plan, please contact us.
To set up Single Sign-On with Azure Active Directory (Azure AD), you will need permissions to create and manage a new Azure AD application.
1. Prepare Ybug for SSO configuration
1.1 Before you can set up the Azure AD SSO application, you must open the Single Sign-On settings page in Ybug. Go to your Team account settings page, click the Single Sign-On tab and check the Enable Single Sign-On checkbox. Leave this window open, you will need this information to complete configuration of the Ybug app in Azure AD.

2. Set up Azure AD for Ybug
2.1 Sign in to the Azure portal using your Azure Active Directory administrator account.
2.2 Navigate to Enterprise applications, select New application and then click New application:

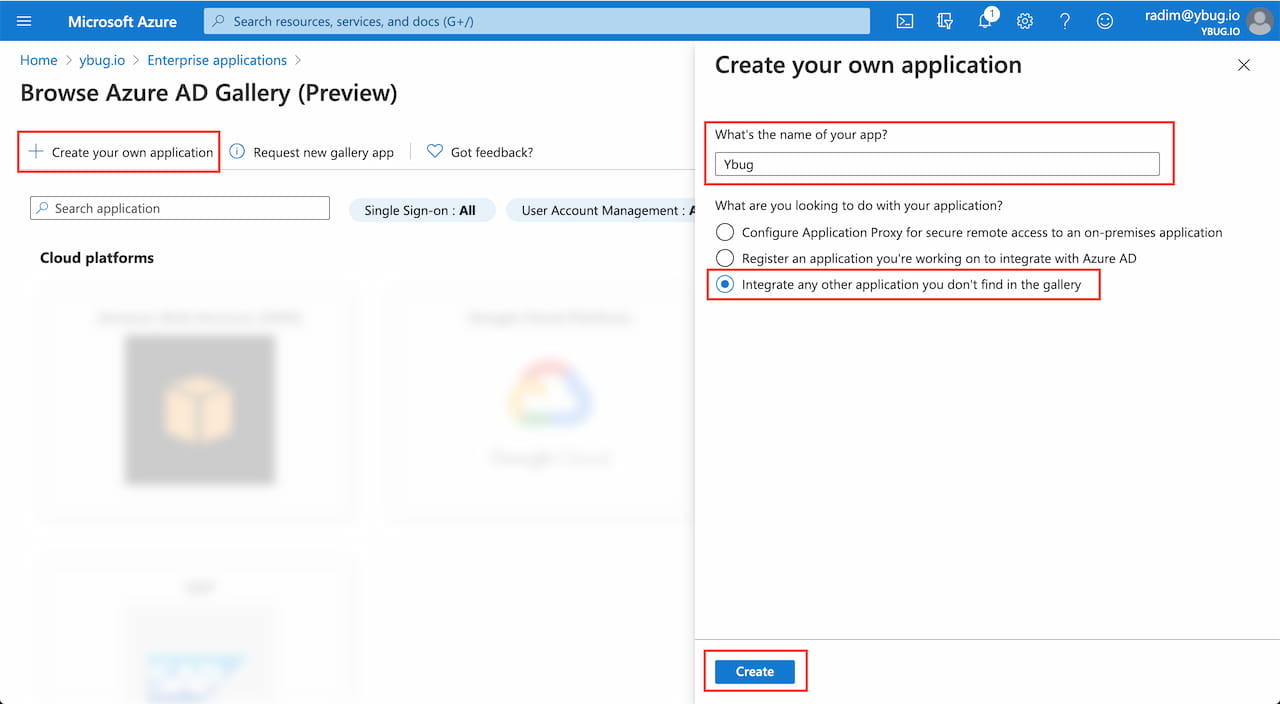
2.3 As Ybug is not yet listed in the Azure Active Directory marketplace, you need to Create your own application. Enter the name of the application, keep Integrate any other application you don't find in the gallery option selected and click Create:
2.4 After your new application is created, go to Single sign-on section and select SAML method from the available options:

2.5 Click Edit on the Basic SAML Configuration pane:

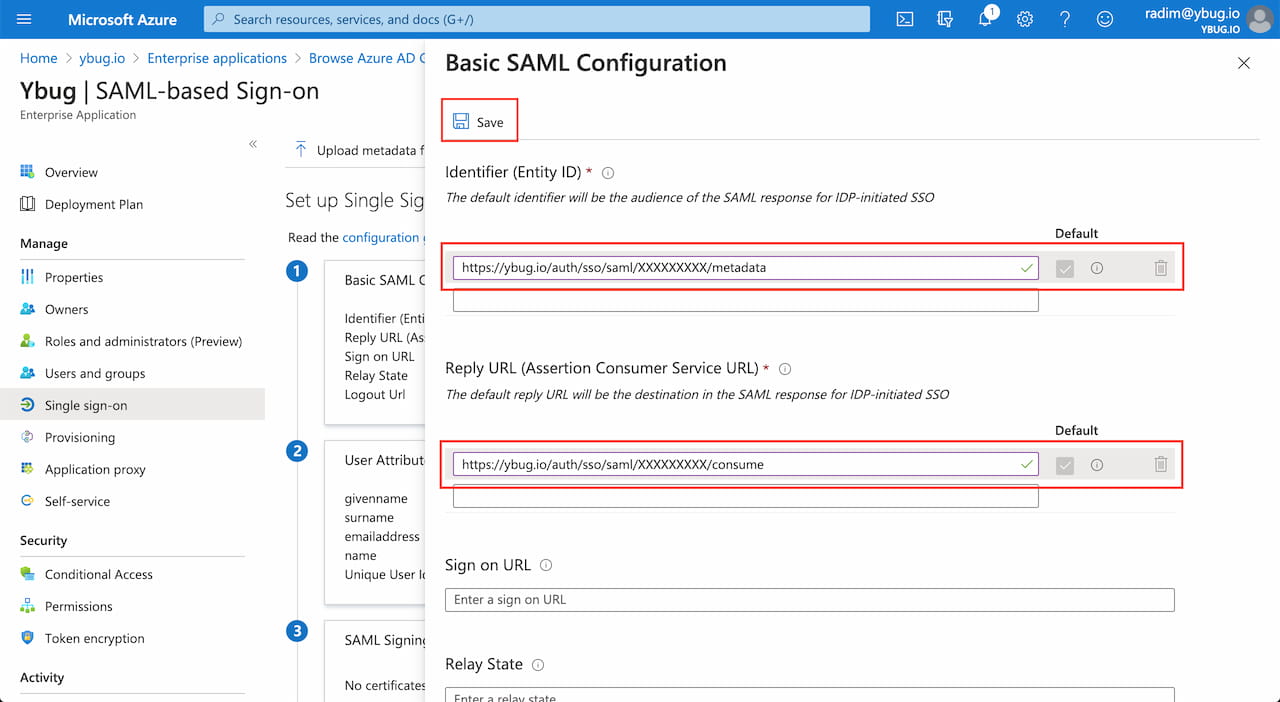
2.6 Configure the SAML integration. Enter the Ybug service provider details from the Ybug Single Sign-On page (from the Step 1). Then click Save.
| Field (in Azure AD) | Value (from Ybug) |
|---|---|
| Identifier (Entity ID) | Entity ID |
| Reply URL (Assertion Consumer Service URL) | Assertion Consumer Service URL |
2.7 Make also sure to set Unique User Identifier to user.mail:

3. Set up Ybug
3.1 In Azure AD on the Set up Ybug section, click the View step-by-step instructions link. Follow these step-by-step instructions and enter SAML Single Sign-On Service URL / SAML Entity ID into Ybug. Download Base64 encoded "SAML Signing Certificate" and enter it's contents into Ybug's Certificate field.
| Field (in Ybug) | Value (from Azure AD) |
|---|---|
| Entity ID | SAML Entity ID |
| SSO URL | SAML Single Sign-On Service URL |
| Certificate | Contents of SAML Signing Certificate - Base64 encoded |


3.2 Then in Ybug click the Save SSO Settings button to enable the Single Sign-On.
4. Assign users
Assign users or groups to your new Ybug SAML application in Azure AD. For more information on how to do it, please refer to the official Azure AD documentation.
Final steps
After successfully setting the SSO, your users should be able to sign in or sign up using your Identity Provider.
- Team members (not owners) with an existing Ybug account with the same email address as their SSO account will be switched to SSO authentication after they first log in with SSO.
- For users who do not have Ybug account yet, a new Ybug account will be provisioned once they log in for the first time (from their Identity Provider).
Do you have any questions?
Contact us in case you have any questions or feedback.
We will be happy to help.